Donations in Monero are very appreciated. Please use:
82cGMSGzFAsEYwF237VaJq1PGCRPbWikfJeewDLftsaR5NDwiVLPBgG1YDy7p1UpLBJnnRv84MeHu6Pz3cV7XHZn4N4T35C for XMR
All donations will be used to help host the site

Donations in Monero are very appreciated. Please use:
82cGMSGzFAsEYwF237VaJq1PGCRPbWikfJeewDLftsaR5NDwiVLPBgG1YDy7p1UpLBJnnRv84MeHu6Pz3cV7XHZn4N4T35C for XMR
All donations will be used to help host the site
It’s surprisingly difficult to rename nodes and pools and other objects on the F5 LTM BIG-IP platform. But not if you’re willing to use the CLI and enable a feature left disabled by default.
SSH into your F5, then launch the TMOS shell with the command tmsh
modify /sys db mcpd.mvenabled value true
then use the “mv ltm” command – to see the available options, type in “mv ltm ?”, but it’s all pretty straightforward.
After you’re done, it’s recommended to disable the feature again
modify /sys db mcpd.mvenabled value false
So, here’s a q-in-q subinterface. If you just want the single vlan instead of a vlan stack, just leave the second line out and apply the ip address to eno2.123 instead (your interface names may be different, look at “ip link list” to see them)
ip link add name eno2.123 link eno2 type vlan proto 802.1q id 123
ip link add name eno2.123.456 link eno2.123 type vlan proto 802.1q id 456
ip addr add 10.1.2.3/24 dev eno2.123.456
So now static IP addresses and routes are configured in the dhcp client daemon settings. Makes sense.
Interface settings go in /etc/dhcpcd.conf, and it looks like:
interface eth0
static ip_address=10.0.0.1/24
static routers=10.0.0.254
static domain_name_servers=10.0.0.20
The static routes go in /lib/dhcpcd/dhcpcd-hooks/40-route
It looks like:
ip route add 192.168.100.0/24 via 192.168.0.2
Because who needs split horizon dns anyway? When you’re using an ASA as your internet gateway, that is.
object network PrimaryServer
host 192.168.1.2
nat (inside,outside) static 2.2.1.2
object network SecondaryServer
host 192.168.1.3
nat (inside,outside) static 2.2.1.3
object network PrimaryServer-ext
host 2.2.1.2
object network SecondaryServer-ext
host 2.2.1.3
nat (inside,inside) source dynamic any interface destination static PrimaryServer-ext PrimaryServer
nat (inside,inside) source dynamic any interface destination static SecondaryServer-ext SecondaryServer
Me
Windows 10 ipv6 is a huge pain in the ass. Here’s how to actually use the static address you actually configured on the interface for that expressed purpose.
1) Open powershell
2) netsh interface ipv6 set interface “<interface name>” routerdiscovery=disabled store=persistent
3) netsh int ipv6 set privacy disabled
4) netsh interface ipv6 delete address interface=”Ethernet whatever” address=<autogenerated address to remove>
5) netsh interface ipv6 set int <interface number> routerdiscovery=disabled
and “netsh interface ipv6 show addresses” to make sure they haven’t come back.
(set a static address first)
This one was a bit of a pain. I’m assuming that you’ve generated the key, the CSR, sent that off to your CA (or signed it yourself), and received the certificate. You’ve also converted the certificate to DER format if necessary, since you’re familiar with openssl.
Here’s the steps I had to go through to import the certificate and the key:
So it turns out there’s been a bug in one of the windows updates, which causes Windows Explorer to crash when you right-click in the left hand pane.
I couldn’t find the fix but I did find the tools to figure it out myself. Anyway, here it is.
You’ll need ShellExView from http://www.nirsoft.net/utils/shexview.html#DownloadLinks – fire that up, then sort by “CLSID Modified” – it’s probably the most recent one there, but just in case it isn’t, this is the culprit here
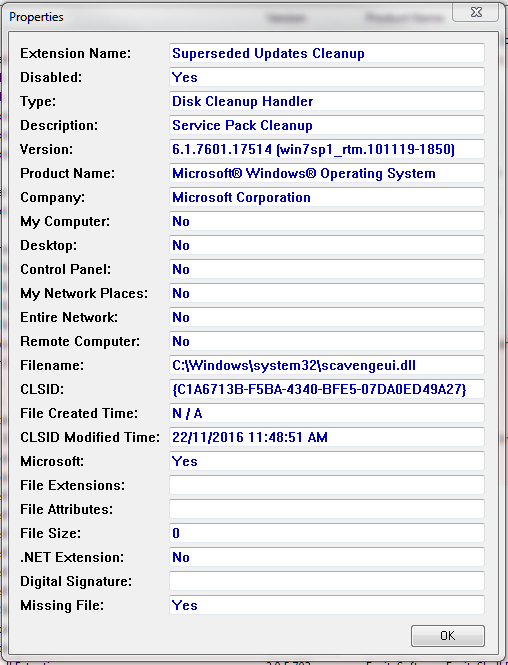
Yep, either a windows update or something left over from one that should have been removed afterwards (but wasn’t).
Step 1: Export your certificate as, or convert it to, a pkcs12 format. If you need to do the latter, try:
openssl pkcs12 -export -out <pfx filename> -inkey <private key file> -in <public certificate file> -certfile <CA certificate bundle or intermediate certificate file used to sign your actual certificate>
Then you need to put it in base64 format to paste it in on the ASA CLI – copy/paste the entire next line including parentheses to do it:
( echo -----BEGIN PKCS12-----; openssl base64 -in <pfx file> ; echo -----END PKCS12-----; ) > <base64 file>
Step 2: Create a trustpoint on the ASA and import the certificate:
crypto ca trustpoint <trustpoint name>
enrollment terminal
fqdn <your anyconnect hostname here>
exit
crypto ca import <trustpoint name> pkcs12 <export password>
openssl genrsa -out <filename to save key to> <bitstrength of key>
eg: to generate a 4096-bit key and save it to “private.key”, run the following command – openssl genrsa -out private.key 4096
openssl ecparam -out <filename to save key to> -name <curve to use> -genkey
eg. to generate a key using the secp521r1 curve (NIST curves seem to be supported by more TLS enabled applications), run the following command – openssl ecparam -out wildcard.fishbowl.lan.key -name secp521r1 -genkey
openssl req -sha256 -new -key <key filename> -out <csr filename>
it is recommended to use -sha256 as -sha1 (default setting) is not considered secure anymore
Example command is: openssl req -new -sha256 -key private.key -out private.csr
openssl ca -keyfile <CA certificate key file> -cert <CA public certificate file> -notext -md sha512 -days <validity length, usually multiples of 365> -in <CSR file> -out <public certificate file>
It is recommended to use -md sha512 for security purposes
Example command is: openssl ca -keyfile rootCA.key -cert rootCA.crt -notext -md sha512 -days 730 -in private.csr -out public.crt
Sidenote: to use a section of your openssl.conf to, for instance, create an intermediate certificate, include the parameter “-extensions v3_intermediate_ca”
openssl req -new -x509 -days <length of validity> -key <keyfile> -out <CA certificate file>
It is recommended to specify a long duration for -days since once your root CA certificate becomes invalid, so do all the certificates it was used to sign.
Example command is: openssl req -new -x509 -days 3650 -key rootCA.key -out rootCA.crt
openssl pkcs12 -export -out <PFX file> -inkey <Private key file> -in <Public certificate file> -certfile <CA file used to sign original public certificate>
Example command is: openssl pkcs12 -export -out client-auth.pfx -inkey private.key -in public.crt -certfile rootCA.crt
openssl x509 -in <certificate file> -text -noout
This will display all the certificate information in the terminal. Hopefully no example command is needed.
Powered by WordPress & Theme by Anders Norén